FREE Cybersecurity Health Check!
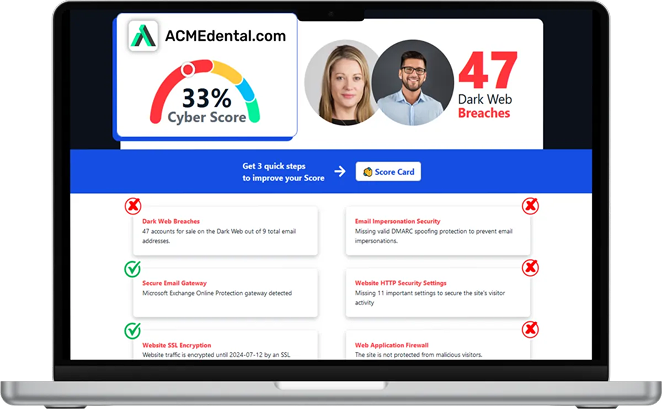
Want to see your Score?
Get it in 30 seconds!
Enter Your Website URL to Get Your Cyber Score Right Now:
Enter Your Website URL to Get Your Cyber Score Right Now:
Stopping Threats, Securing Systems, Protecting Business Continuity
At Compliance Cybersecurity Solutions, our security trained and certified team provides robust cybersecurity to keep your business safe, even if you're new to digital protection. Our expert strategies ensure your systems stay online, block unauthorized access, and shield your data from threats around the clock. Tailored for industries like healthcare, engineering, and defense, our services minimize downtime, prevent costly ransom demands, and protect against legal risks. With constant monitoring, we keep your business secure from ever-evolving cyber threats utilizing Zero Trust.
Less Downtime, Lower Risk, And Fewer Security Surprises
Protection that starts with policy, not just tools or alerts.
IT services that block ransomware, phishing, and account takeovers.
Coverage across endpoints, networks, email, and cloud platforms.
Controls that limit access, enforce MFA, and log user behavior.
Real-time monitoring backed by expert human intervention.
Cybersecurity services designed for healthcare and regulated industries.
Support that helps meet insurance, contract, and audit requirements.
How We Build Cybersecurity Into Every Layer Of Your IT
Our cybersecurity services are engineered to actively reduce risk, meet compliance requirements, and provide continuous protection across your entire environment. We do not rely on default settings or one-time setups. We implement layered defenses supported by policies, tools, and accountability.
Threat Prevention Strategy
We deploy SentinelOne, ThreatLocker, and other platforms to block malware, ransomware, and unauthorized access before they disrupt operations, steal data, or damage business continuity.
Email And Identity Controls
Cisco DUO, Avanan, and MFA policies stop phishing, spoofing, and account takeovers across devices and applications, protecting communications, user credentials, and internal business systems.
24/7 Monitoring And Response
With tools like SaaS Alerts, Vulscan, and PILLR SOC, we detect threats in real time and respond before they escalate, ensuring immediate action, minimal disruption, and ongoing peace of mind.
Framework-Aligned Security
All configurations are mapped to HIPAA, CMMC, FTC Safeguards, and other frameworks to support audits and reduce liability, ensuring legal alignment, reduced risk, and enterprise-level protection.

Why You Might Need Help
Staying compliant while protecting sensitive systems is not just difficult, it is constant. Many businesses find themselves exposed to risk they cannot easily detect. Without specialized help, critical updates are missed, policies fall out of sync, and security gaps go unnoticed until something goes wrong.
Whether you are preparing for a HIPAA audit, pursuing CMMC certification, or just trying to stop phishing emails from reaching staff, our team can help. CCS was built to support businesses like yours with IT services that combine technical defense, policy enforcement, and hands-on accountability, so you do not have to figure it out alone.
Why Clients Trust CCS With Their Cybersecurity Needs
We are not just IT providers, we are cybersecurity specialists with decades of proven experience protecting regulated businesses. Our services are built around the realities of modern attacks, compliance obligations, and the need for clear, coordinated protection. Every system we secure is treated as critical because our clients cannot afford failures.
Our team designs, implements, and actively manages cybersecurity services that align with HIPAA, CMMC, FTC Safeguards, and more.

Cybersecurity Consulting & Services
Real-World Cybersecurity Built Around Your Industry Risks
We provide cybersecurity services that go beyond software installations. Our team evaluates your existing defenses, identifies gaps, and builds a strategy tailored to your industry and compliance obligations. Using platforms like SentinelOne, ThreatLocker, and PILLR SOC, we help clients block attacks, monitor systems, and maintain long-term protection.
We focus on the combination of policy, access control, and technical hardening to create a full-spectrum cybersecurity plan designed to hold up under scrutiny and stop real threats before they take hold.
Risk assessments and technical reviews align your defenses with your compliance requirements.
Endpoint protection, email filtering, MFA, and access rules close the most common attack paths.
We monitor continuously and respond quickly, helping prevent small issues from becoming major incidents.
IT Support Helpdesk Services
Responsive Support That Keeps Systems Running And Users Secure
Our IT support team is built for businesses that operate in sensitive environments. When you call, we answer, and when you need help, we act fast. From login problems to workstation performance and email issues, we resolve problems while actively and consistently preserving compliance integrity and security policy enforcement.
Our helpdesk services are never disconnected from your broader cybersecurity strategy. Every ticket is handled with context, professionalism, and a focus on long-term stability and risk reduction.
We respond quickly with technical help that respects your policies and compliance needs.
Remote tools allow for secure support without compromising system or data access.
Every issue is documented, resolved, and tracked as part of your IT and security posture.
Security Backed By Strategy, And Real Accountability
At CCS, we do more than deploy tools. We deliver cybersecurity services that align with compliance and reduce risk across your environment. Our clients count on us to understand their industry, implement protections that actually work, and stay involved after the setup is complete.
Risk-Based Configuration
Every setting, tool, and policy is based on what protects your business, not just what looks good on paper. We assess your specific environment and risks before implementing technology, ensuring defenses are relevant and effective. Instead of generic checklists, we focus on what actually reduces threat impact and exposure.
Proactive Threat Prevention
We use PILLR SOC, SaaS Alerts, Vulscan, and more to monitor suspicious activity before it causes disruption. These tools give us real-time visibility into endpoints, user behavior, and vulnerabilities. We detect anomalies early and take action before problems escalate—tracking patterns and closing gaps over time.
Audit-Ready Systems
Our IT services are documented, policy-aligned, and built to meet HIPAA, CMMC, and FTC Safeguards. Everything from passwords to backups is tracked and framework-aligned, helping you avoid surprises during audits. You get fewer headaches, faster compliance, and confidence that your systems will hold up under scrutiny.
Tuned To Your Reality
We don’t copy-paste strategies—we build around your size, systems, and risks. Our services match how your team works, what data you handle, and what regulations apply. Whether you’re growing, shifting, or in a sensitive industry, we provide tailored protection that fits your goals.
Frequently Asked Questions
What’s The Role Of Cybersecurity In Compliance?
We specialize in IT services that combine cybersecurity, compliance consulting, and helpdesk support for regulated organizations.
How Do You Know What Threats To Focus On?
We support healthcare providers, defense contractors, financial firms, engineering groups, law offices, and other compliance-driven businesses.
Can You Help After A Breach Or Security Incident?
We support HIPAA, CMMC L1 and L2, FTC Safeguards, SOC2, PCI, NIST, and cyber insurance readiness through technical and policy implementation.
What Makes CCS Different From Other Cybersecurity Providers?
We focus exclusively on regulated industries and align every service to compliance requirements with hands-on support, expert guidance, and clear documentation.
Is Endpoint Protection Enough On Its Own?
No. Endpoint tools are one layer. You also need email filtering, MFA, identity controls, policy enforcement, and monitoring to defend your environment effectively.